Unraveling the Intricate Web of RISC-V Architecture
Definition and Background
RISC-V Architecture is an open-source instruction set architecture (ISA) that is designed to be simple, modular, and extensible. It is a type of computer architecture that defines the instructions and operations that a central processing unit (CPU) can execute. RISC-V stands for Reduced Instruction Set Computing, where the focus is on minimizing the number of instructions and keeping them simple and efficient.
The RISC-V architecture is gaining popularity due to its open standard nature, allowing for easy customization and innovation. It is not tied to any specific company or proprietary software, making it a flexible choice for various applications. RISC-V supports both 32-bit and 64-bit computing, allowing for scalability and compatibility with different systems.
The origins of RISC-V can be traced back to the RISC project at the University of California, Berkeley. The project aimed to develop a new generation of computer architecture, which led to the creation of the first RISC processor, known as the Berkeley RISC-1.
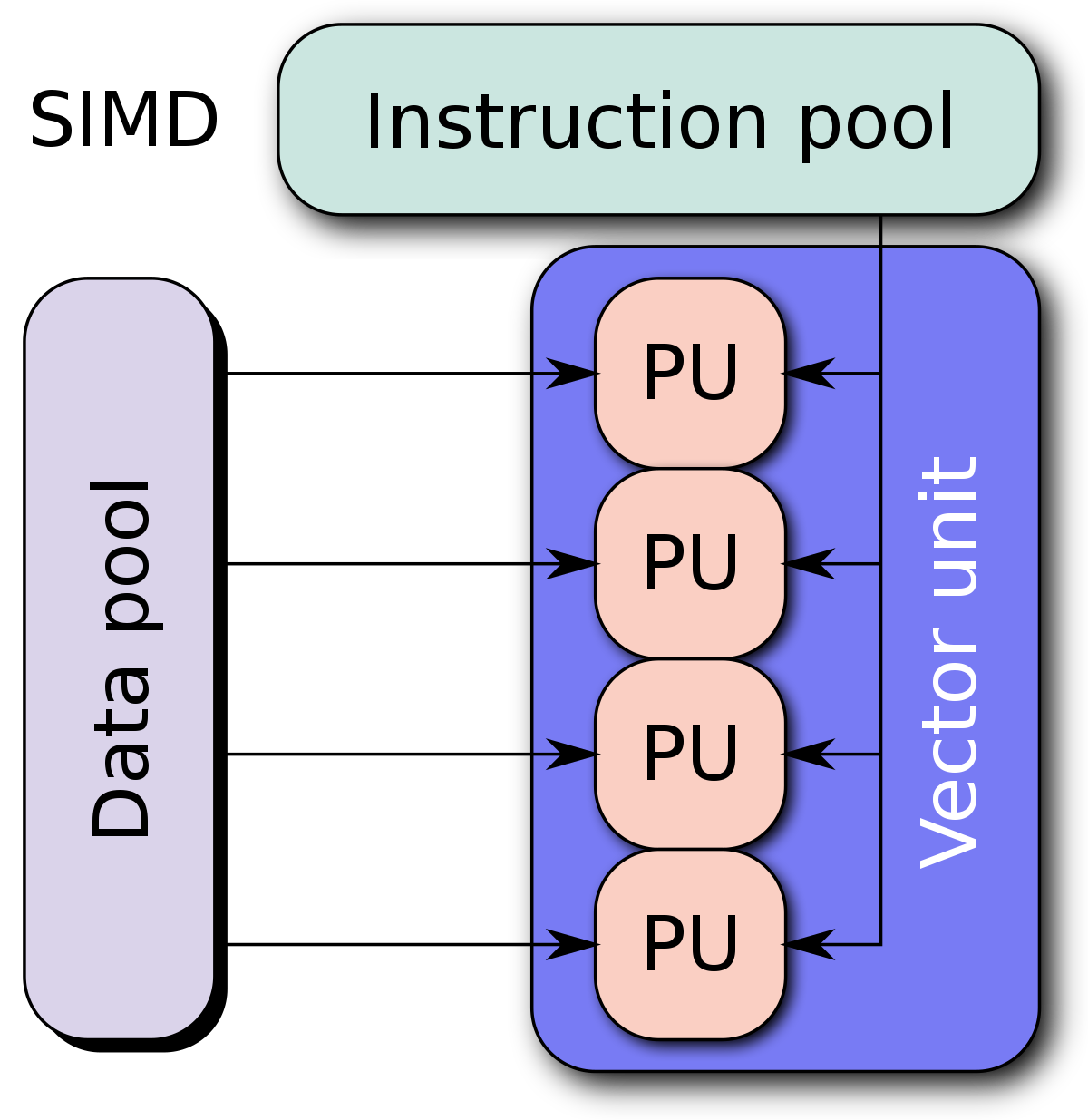
One of the key advantages of RISC-V is its simplicity, which makes it easier to understand and implement. It also allows for efficient energy use, making it suitable for low-power electronics and embedded systems. Additionally, RISC-V’s modular design enables the development of specialized processors for specific tasks, such as vector processors for parallel computing or microcontrollers for embedded systems.
The open-source nature of RISC-V encourages collaboration and software development. It allows developers to freely access and modify the architecture, leading to a vibrant ecosystem of open-source software and tools. This openness also helps in debugging and software development, as developers can easily analyze and modify the underlying architecture.
Rationale and History
The RISC-V architecture is an open-source instruction set architecture (ISA) that has gained significant attention in recent years. Its development can be traced back to the early 1980s when researchers at the University of California, Berkeley, began exploring the concept of Reduced Instruction Set Computing (RISC).
Unlike traditional complex instruction set computing (CISC) architectures, RISC-V focuses on simplicity and efficiency. It is designed to be modular and scalable, making it suitable for a wide range of applications from embedded systems to supercomputers.
The history of RISC-V is closely tied to the development of other architectures such as MIPS and ARM. In fact, many of the key contributors to RISC-V were involved in the development of these architectures. However, RISC-V sets itself apart by being an open standard, allowing anyone to use and modify the architecture without any licensing or royalty fees.
With its open-source nature, RISC-V has gained popularity among researchers, developers, and companies looking for a flexible and customizable architecture. It has been embraced by various industries, including data centers, personal computers, and low-power electronics, due to its efficient energy use and innovation potential.
Furthermore, RISC-V has a thriving ecosystem with a wide range of development tools, compilers, and operating systems such as Ubuntu. This makes it easier for developers to work with RISC-V and contributes to its growing adoption.
Understanding the rationale and history behind the RISC-V architecture is crucial for anyone interested in delving into the world of Linux training. By familiarizing themselves with this open-source architecture and its evolution, individuals can gain valuable insights into the principles of processor design, parallel computing, and efficient energy use.
RISC-V Foundation and International

The RISC-V Foundation is an international organization that promotes the development and adoption of the RISC-V architecture. RISC-V is an open-source instruction set architecture (ISA) that is gaining popularity in the computer hardware industry. It is designed to be simple, modular, and scalable, making it suitable for a wide range of applications, from embedded systems to supercomputers.
The RISC-V architecture supports both 32-bit and 64-bit computing, and it can be implemented on various processor designs, including microcontrollers, multi-core processors, and vector processors. It is also compatible with different operating systems, such as Linux and Ubuntu.
One of the key advantages of the RISC-V architecture is its open-source nature. Unlike proprietary architectures like ARM or MIPS, RISC-V allows for collaboration and innovation without the need for royalty payments or strict licensing agreements. This openness encourages the development of new ideas and the sharing of knowledge within the community.
For those interested in learning more about the RISC-V architecture and its implementation, Linux training can be a valuable resource. Linux is an open-source operating system that is widely used in the computer industry. It provides a flexible and customizable platform for developing and testing RISC-V-based systems.
By gaining experience with Linux and understanding how it interacts with the RISC-V architecture, individuals can develop the skills needed to work with RISC-V-based systems, debug issues, and optimize performance. Linux training can also provide insights into other important areas, such as software composition analysis, security, and software licensing.
For more information about the RISC-V architecture, its applications, and the RISC-V Foundation, refer to reliable sources like Wikipedia or the official RISC-V Foundation website. These resources can provide in-depth explanations, technical specifications, and updates on the latest developments in the field.
Design and ISA
| Design and ISA in RISC-V Architecture | |
|---|---|
| Design | Instruction Set Architecture (ISA) |
|
The design of RISC-V architecture follows a simple and modular approach, aiming to provide a flexible and scalable solution for a wide range of applications. Some key design principles include:
|
RISC-V uses a reduced instruction set architecture (ISA) which provides a standardized set of instructions and registers for software development. The key features of RISC-V ISA include:
|
|
The design of RISC-V architecture promotes simplicity and ease of implementation, making it suitable for a variety of devices ranging from embedded systems to high-performance servers. |
The flexibility and extensibility of RISC-V ISA allow developers to customize the instruction set according to their specific requirements. This enables the development of specialized accelerators and co-processors for various applications. |
Profiles, Platforms, and Register Sets
Profiles in RISC-V refer to sets of instructions that are specifically tailored for certain types of applications or environments. For example, the Embedded Profile includes instructions that are optimized for embedded systems, while the Linux Profile includes instructions that are optimized for running the Linux operating system. These profiles allow developers to customize their RISC-V processors based on their specific needs.
Platforms in RISC-V are a set of standard interfaces and hardware components that define the system architecture. They provide a common framework for software developers to build applications and operating systems that can run on different RISC-V platforms. This allows for greater compatibility and portability across different RISC-V systems.
Register Sets in RISC-V are a collection of registers that store data and control information within the processor. Each register has a specific purpose, such as storing program counters, data, and status flags. RISC-V allows for different register sets to be defined, depending on the specific requirements of the application or platform.
Understanding the profiles, platforms, and register sets in RISC-V is crucial for anyone looking to work with or develop RISC-V processors. By familiarizing oneself with these components, individuals can gain a deeper understanding of the architecture and make informed decisions when it comes to processor design and software development.
If you are interested in learning more about RISC-V architecture and how to work with it, consider taking Linux training courses. Linux is a popular operating system for RISC-V processors, and having knowledge and experience with Linux can greatly enhance your skills in this field. Linux training courses can provide you with the necessary knowledge and hands-on experience to effectively work with RISC-V processors and develop software for them.
Memory Access and Immediates
| Topic | Description |
|---|---|
| Memory Access | Memory access is a crucial aspect of any computer architecture, including RISC-V. It refers to the process of reading from or writing to the system’s memory. In RISC-V, memory access can be performed using load and store instructions. Load instructions transfer data from memory to a register, while store instructions write data from a register to memory. |
| Immediates | Immediates are constants or literal values used in instruction operands. They provide immediate data to be used by the instruction. In RISC-V, immediates can be used to specify immediate values for arithmetic and logical operations. They are typically represented as 12-bit or 20-bit signed or unsigned values. |
Subroutine Calls and Branches
In RISC-V, a subroutine call is a mechanism used to transfer control to a different part of a program and then return to the original location once the subroutine has completed its execution. This is achieved through the use of the jal (jump and link) instruction, which stores the return address in a register and jumps to the target subroutine.
Branch instructions in RISC-V allow for conditional execution based on a specified condition. These instructions enable the program to make decisions and alter the control flow accordingly. Various branch instructions such as beq (branch if equal), bne (branch if not equal), blt (branch if less than), and bge (branch if greater or equal) provide flexibility in controlling program execution.
Understanding subroutine calls and branches is crucial for programming in the RISC-V architecture. These concepts are fundamental to writing efficient and optimized code.
Subroutine calls and branches are widely used in various domains, ranging from embedded systems and microcontrollers to supercomputers and data centers. Their efficient implementation is essential for achieving high-performance computing.
To master RISC-V architecture and effectively utilize its features, it is recommended to undergo Linux training. Linux provides a robust and versatile environment for developing and running RISC-V applications. Additionally, Linux training equips individuals with the necessary skills to leverage open-source software and tools, which are prevalent in the RISC-V ecosystem.
By gaining proficiency in RISC-V subroutine calls and branches, individuals can enhance their understanding of computer hardware and microarchitecture. This knowledge is valuable for tasks such as debugging, optimizing code, and implementing advanced features like floating-point arithmetic.
Resources like Wikipedia, IEEE 754 specifications, and open-source architecture documentation can provide further insights into the intricacies of RISC-V subroutine calls and branches. Additionally, tools like compilers and software composition analysis can aid in the development and analysis of RISC-V software.
To ensure compliance with intellectual property and licensing requirements, individuals should familiarize themselves with open-source licenses, patents, copyrights, and royalty payments associated with RISC-V and associated technologies.