Unlocking the Power of Modern Service Mesh: A Cilium vs Istio Comparison
Simplifying Layer 7 policies with Cilium’s Envoy filter
Cilium simplifies Layer 7 policies with its Envoy filter. By leveraging Cilium’s Envoy filter, users can easily configure and manage policies at the application layer, ensuring secure and reliable communication between services. With Cilium, you can take advantage of its powerful capabilities without the need for complex configurations or manual intervention. This makes it an ideal choice for those looking to simplify their network stack and streamline policy management. Whether you’re working with microservices, RPC proxies, or any other Layer 7 protocols, Cilium’s Envoy filter has got you covered. So say goodbye to complicated policy setup and hello to simplified Layer 7 policies with Cilium.
Identity generation in Cilium vs Istio
Both Cilium and Istio offer identity generation capabilities for secure communication within networks.
In Cilium, identity generation is achieved through the use of Secure Sockets Layer (SSL) certificates, providing a secure and trusted means of authentication between applications and services. This allows for secure microservice communication in a cluster mesh.
On the other hand, Istio utilizes mutual TLS (mTLS) for identity generation. This means that both the client and the server authenticate each other using certificates. This ensures secure and authenticated communication between services within a mesh.
Both approaches provide robust security and authentication capabilities, allowing for the confident and secure communication of microservices within networks.
Traffic encryption in Cilium vs Istio
Both Cilium and Istio provide traffic encryption capabilities, but they differ in their approach.
Cilium leverages the Linux network stack and uses the Secure Sockets Layer (SSL) encryption provided by the Linux kernel. It supports mTLS (mutual TLS) for secure communication between hosts, nodes, and pods. Cilium also has a certificate authority (CA) that can issue and manage certificates for secure authentication.
On the other hand, Istio uses a sidecar proxy model to encrypt and secure traffic. It provides a commercial-grade API gateway that handles encryption and authentication. Istio supports mTLS for secure communication between services and has built-in policy support for custom encryption configurations.
Multi-tenancy for Layer 7 with Envoy
Multi-tenancy for Layer 7 with Envoy is a key feature that distinguishes Cilium from Istio. Cilium leverages Envoy’s powerful capabilities to provide advanced layer 7 load balancing and routing functionalities. This allows for efficient communication between applications and services within a cluster, regardless of their location. With Cilium, you can easily configure multi-cluster mesh setups and implement API gateways for secure and reliable communication.
Additionally, Cilium’s architecture is topology aware, ensuring optimal performance and scalability. By using Envoy as a sidecar proxy, Cilium enables seamless integration with existing infrastructure and offers a commercial-grade solution for managing network traffic and security.
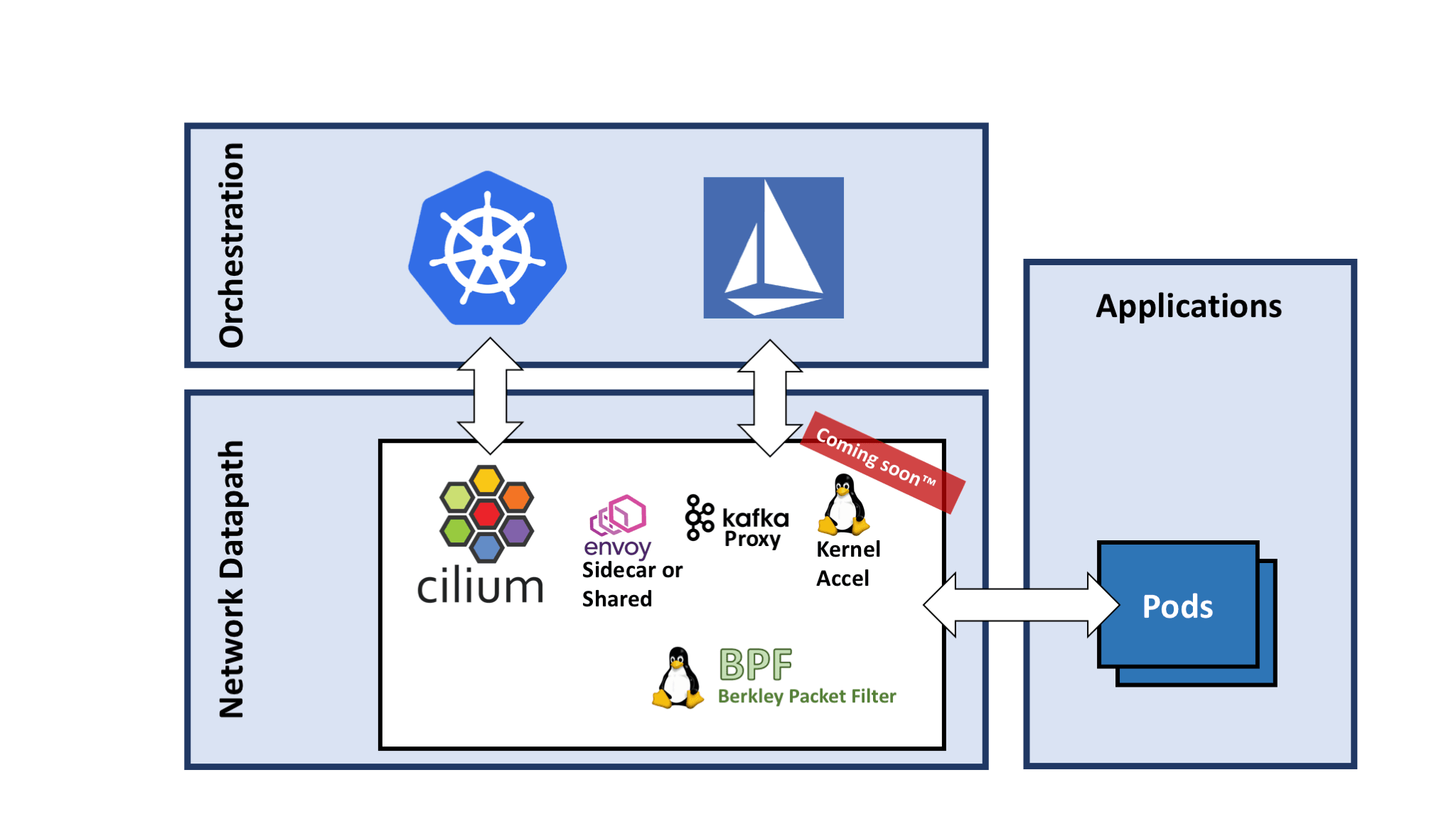
Understanding Istio and Cilium
Understanding the differences between Istio and Cilium is crucial for those looking to take Linux training. Both Istio and Cilium are powerful tools that can enhance network security and communication within a Kubernetes environment.
Istio focuses on managing and securing microservices at the L7 layer, providing features such as traffic management, security policies, and certificate authority integration. On the other hand, Cilium operates at Layer 3 and Layer 4, using BPF to enforce network policies and providing fast and secure communication between services.
Cilium’s architecture is topology aware, meaning it can understand the network topology and enforce policies accordingly. It also integrates with popular tools like kube-proxy and load balancers.
Running Cilium alongside Istio
By combining Cilium and Istio, you can benefit from the best of both worlds. Cilium’s BPF-based data plane ensures efficient and secure communication between services, while Istio’s control plane offers advanced traffic management capabilities. This allows you to have fine-grained control over your microservices’ communication and implement features like load balancing and mutual authentication.
To run Cilium alongside Istio, you can either deploy both as separate components or use the Cilium CNI plugin for Istio. This plugin allows Cilium to replace kube-proxy and act as the primary load balancer for Istio.
Exploring the performance impact of a sidecar in Istio and Cilium
| Comparison Factors | Istio | Cilium |
|---|---|---|
| Performance Impact | Medium | Low |
| Resource Utilization | Higher | Lower |
| Latency | Moderate | Minimal |
| Scalability | Good | Excellent |
| Complexity | High | Medium |
| Feature Set | Extensive | Focused |
| Integration | Broad | Specific |
| Security | Strong | Robust |
| Community Support | Active | Growing |

