Welcome to the world of blockchain technology, where decentralized networks and secure transactions are revolutionizing the way we interact with digital assets. In this tutorial, we will explore the basics of blockchain technology for beginners looking to understand this innovative technology. Let’s dive in!
What is Blockchain Technology?
Blockchain Technology is a decentralized system that records transactions across multiple computers. It uses cryptography to secure data and prevent fraud. Each transaction is added to a block that forms a chain, hence the name Blockchain.
Unlike traditional systems, Blockchain Technology operates on a peer-to-peer network, eliminating the need for intermediaries like banks. This allows for faster and more secure transactions.
This technology is the backbone of cryptocurrencies like Bitcoin and Ethereum, but its applications go beyond just digital currency. It can be used for supply chain management, identity management, and more.
Importance of Blockchain
Blockchain technology is crucial for ensuring secure and transparent transactions in a decentralized manner. It eliminates the need for intermediaries and reduces the risk of fraud and tampering with data. With the use of cryptographic hash functions and encryption, blockchain provides a secure platform for peer-to-peer transactions.
Blockchain technology is not limited to just cryptocurrencies like Bitcoin or Ethereum. It has the potential to revolutionize various industries such as supply chain management, identity management, and even e-commerce. By leveraging blockchain technology, businesses can streamline operations, reduce costs, and enhance security.
Understanding the importance of blockchain is essential for anyone looking to stay ahead in the rapidly evolving digital landscape. Whether you are an entrepreneur, a developer, or simply interested in learning more about this technology, grasping the fundamentals of blockchain is key to unlocking its full potential. Start your journey into the world of blockchain technology today and pave the way for a more secure and efficient future.
Cryptocurrency Overview
Cryptocurrency is a digital or virtual form of currency that uses encryption for security. It operates on a decentralized network called blockchain, which records all transactions in a secure and transparent manner. Bitcoin, Ethereum, and Dogecoin are popular cryptocurrencies that utilize this technology for peer-to-peer transactions.
Blockchain technology ensures trusted timestamping and encryption for secure transactions. It eliminates the need for intermediaries like banks, making payments faster and more efficient. Smart contracts, used by platforms like Cardano and Ethereum Classic, automate processes on the blockchain.
Cryptocurrencies can be stored in a digital wallet and used for various purposes, including online purchases, investments, and more. Understanding blockchain technology is crucial for anyone interested in the world of digital currency.
Types of Blockchain Wallets
When it comes to storing your cryptocurrencies, there are different types of blockchain wallets to choose from. The most common ones include hardware wallets, which are physical devices that store your digital currencies offline for added security. Software wallets, on the other hand, are applications or online services that store your cryptocurrencies on your computer or mobile device.
Another type of blockchain wallet is a paper wallet, which involves printing out your private keys and public addresses on a piece of paper. This method provides a high level of security as it is not connected to the internet. Lastly, there are online wallets, which are web-based services that store your cryptocurrencies on the cloud.
Each type of wallet has its own benefits and drawbacks, so it’s important to choose the one that best fits your needs and level of security.
Ethereum Explained
Ethereum is a decentralized platform that enables smart contracts and peer-to-peer transactions using its native cryptocurrency, Ether. This platform allows developers to create decentralized applications (dApps) that run on the blockchain.
One of the key features of Ethereum is its ability to execute code automatically when certain conditions are met, thanks to smart contracts. These contracts are self-executing and provide a high level of security and trust.
To participate in the Ethereum network, users need a digital wallet to store their Ether and interact with dApps. Transactions on the Ethereum blockchain are verified using a consensus mechanism called Proof of Work (PoW).
Overall, Ethereum revolutionizes the way we think about transactions and contracts by enabling secure, transparent, and tamperproof interactions on a decentralized network. It opens up endless possibilities for innovation in various industries, from finance to real estate.
Whether you’re a developer looking to build decentralized applications or a user interested in the future of blockchain technology, Ethereum offers a world of opportunities to explore and utilize.
Comparison: Bitcoin vs Ethereum
Bitcoin and Ethereum are two prominent **cryptocurrencies** that operate on blockchain technology. Bitcoin was created in 2009 by an **unknown person** or group of people under the pseudonym Satoshi Nakamoto. It was designed as a **peer-to-peer** system for **electronic cash** transactions without the need for a central authority. Ethereum, on the other hand, was proposed by Vitalik Buterin in late 2013 and went live in 2015. It is a decentralized platform that enables **smart contracts** and **distributed applications** (dApps) to be built and run without any downtime, fraud, control, or interference from a third party.
Bitcoin’s primary focus is on being a **digital currency** for secure and anonymous transactions. Its blockchain is mainly used for financial transactions like **payments** and **money transfers**. Ethereum, on the other hand, is more versatile and allows for the development of **smart contracts** and decentralized applications. Its blockchain supports the creation and execution of **smart contracts**, which are self-executing contracts with the terms of the agreement between buyer and seller being directly written into lines of code.
Ethereum Mining Basics
Ethereum mining is the process of validating transactions and adding them to the Ethereum blockchain. Miners use powerful computers to solve complex mathematical puzzles, which requires a significant amount of computational power. In return for their efforts, miners are rewarded with newly minted Ether coins and transaction fees.
To start mining Ethereum, you will need a computer with a powerful graphics processing unit (GPU) and mining software. You will also need to join a mining pool, which allows multiple miners to combine their computational power to increase their chances of solving a block.
Once you have set up your mining rig and joined a pool, you can start mining Ethereum by running the mining software on your computer. Keep in mind that mining can be energy-intensive and may not always be profitable, so it’s important to carefully consider the costs involved before getting started.
Smart Contracts in Blockchain
Smart contracts are self-executing contracts with the terms of the agreement directly written into lines of code. These contracts run on the blockchain, which ensures security, transparency, and efficiency in transactions. One of the key benefits of smart contracts is that they eliminate the need for intermediaries, reducing costs and increasing speed.
With smart contracts, parties can automate processes such as payments, transfers, and record-keeping. This technology has revolutionized various industries, including e-commerce, finance, and supply chain management. By leveraging cryptography and decentralized networks, smart contracts provide tamper-proof and secure transactions.
Blockchain platforms like Ethereum and Cardano are popular choices for creating and executing smart contracts. These platforms offer tools and frameworks for developers to build decentralized applications (*dApps) and implement smart contracts. Understanding smart contracts is essential for anyone looking to explore the potential of blockchain technology.
Understanding Dogecoin
Dogecoin is a **cryptocurrency** that was created as a joke in 2013 but has since gained a significant following. It is based on the same technology as Bitcoin, using a **blockchain** to record transactions. Dogecoin transactions are **peer-to-peer**, meaning they are sent directly from one user to another without the need for an intermediary. This makes transactions faster and cheaper compared to traditional banking systems.
One of the key features of Dogecoin is its **decentralized** nature, meaning that no single entity has control over the network. This makes it resistant to censorship and tampering, providing a level of security that traditional payment systems cannot match. Dogecoin can be used to purchase goods and services online, or simply as a form of digital **money** for transactions between individuals.
Understanding Dogecoin is a great way to get started with **blockchain** technology, as it provides a simple and fun introduction to the world of cryptocurrencies. Whether you are looking to invest in Dogecoin or simply curious about how blockchain technology works, learning about Dogecoin can be a valuable first step.
Dogecoin vs Bitcoin
Dogecoin and Bitcoin are two popular cryptocurrencies that operate on blockchain technology.
Bitcoin is the first and most well-known cryptocurrency, created by an unknown person or group of people under the pseudonym Satoshi Nakamoto. It is often referred to as digital gold due to its scarcity and store of value.
Dogecoin was created as a joke based on the popular “Doge” meme but has gained significant popularity and value over the years. It is known for its community-driven approach and low transaction fees.
Both cryptocurrencies use blockchain technology to record transactions in a secure and transparent manner. They also rely on a decentralized network of nodes to validate and confirm transactions.
While Bitcoin is considered a more stable and established cryptocurrency, Dogecoin has gained attention for its meme culture and community engagement. Both have their own unique features and use cases in the world of digital assets.
Dogecoin Mining Process

Mining Dogecoin involves using computer hardware to solve complex mathematical equations in order to validate transactions on the blockchain. Miners compete to be the first to solve these equations, with the winner receiving a reward in Dogecoin.
To start mining Dogecoin, you will need a computer with a strong processing power, specialized mining software, and a secure wallet to store your earnings. Once you have all the necessary tools, you can join a mining pool to increase your chances of earning rewards.
Mining Dogecoin can be a profitable venture, but it also requires a significant investment in hardware and electricity costs. It is important to carefully consider the risks and rewards before diving into the world of cryptocurrency mining.
Digital Dogecoin Wallets
When choosing a digital wallet, make sure to consider factors such as security features, user interface, and compatibility with your device. Popular options include hardware wallets for added security and mobile wallets for convenience on the go.
It’s important to back up your wallet’s private keys to prevent the risk of losing access to your funds. Always keep your wallet software up to date to protect against potential security vulnerabilities.
By utilizing a digital Dogecoin wallet, you can securely store, send, and receive your cryptocurrency with ease, making it a valuable tool for navigating the world of blockchain technology.
Industries Disrupted by Blockchain
Smart contracts on platforms like Ethereum Classic and Cardano automate agreements, reducing the need for manual intervention. Web3 technology is shaping the future of decentralized applications and services. Cryptocurrencies like Bitcoin, Binance Coin, and Tether are revolutionizing the payment system.
Blockchain technology offers new opportunities for entrepreneurship and innovation, while also addressing issues like censorship and fraud. By leveraging blockchain, industries can streamline processes, enhance security, and improve trust among stakeholders. Embracing blockchain is essential for staying competitive in today’s digital economy.
Emerging Blockchain Applications
– From **smart contracts** to **non-fungible tokens**, blockchain technology is being utilized for a wide range of applications beyond just cryptocurrencies.
– Industries such as banking, supply chain management, healthcare, and more are exploring the benefits of blockchain for improving efficiency and security.
– By leveraging decentralized networks and cryptographic hash functions, blockchain technology offers a tamperproof way to store and verify data.
– Whether you are an entrepreneur looking to streamline your operations or a consumer seeking a more secure payment system, understanding blockchain applications is essential in today’s digital economy.
Becoming a Blockchain Developer
To become a **Blockchain Developer**, you will need to start with a strong foundation in **Linux training**. This operating system is widely used in the blockchain industry, so mastering it is crucial. Once you have a good grasp of Linux, you can move on to learning about **blockchain technology** and its various components. Understanding the **Bitcoin protocol** and **smart contracts** is essential for any aspiring blockchain developer. Additionally, familiarize yourself with **peer-to-peer transactions** and **trusted timestamping** to gain a comprehensive understanding of the technology.
When delving into blockchain development, consider exploring platforms like **Cardano** and tools like **Web3** to expand your knowledge. Keep up with industry trends by following platforms like **Binance** and **Ripple Labs**. Understanding concepts like **decentralization** and **tamperproofing** will also be crucial in your journey.
NFTs Explained
NFTs, or Non-Fungible Tokens, are unique digital assets that are stored on a blockchain. Unlike cryptocurrencies like Bitcoin, which are fungible and interchangeable, NFTs are one-of-a-kind and cannot be replicated or exchanged for an equal value. NFTs can represent a variety of digital assets, such as artwork, music, videos, and even virtual real estate.
Blockchain technology is the underlying technology that powers NFTs and ensures their authenticity and ownership. Each NFT is stored on a decentralized ledger, making it tamperproof and secure from theft. This technology eliminates the need for intermediaries like banks and allows for direct peer-to-peer transactions.
Smart contracts, which are self-executing contracts with the terms of the agreement directly written into code, are often used to facilitate NFT transactions. Platforms like Cardano and Ripple Labs are popular choices for creating and trading NFTs due to their advanced blockchain capabilities.
Solidity Programming Guide
Solidity is a high-level programming language used for writing smart contracts on blockchain platforms like Ethereum. Understanding Solidity is essential for creating decentralized applications and executing peer-to-peer transactions securely.
When learning Solidity, it is crucial to grasp concepts like variables, functions, and control structures. Additionally, familiarizing yourself with Ethereum’s gas mechanism and security best practices will ensure your smart contracts are efficient and secure.
Future of Shiba Inu Coin
The future of Shiba Inu Coin looks promising as it continues to gain popularity in the cryptocurrency market. With its strong community support and growing adoption, this meme-based token has the potential to establish itself as a prominent player in the industry.
One of the key factors driving the success of Shiba Inu Coin is its use of blockchain technology. Blockchain technology offers a decentralized and secure platform for peer-to-peer transactions, making it an ideal solution for cryptocurrencies like Shiba Inu.
As blockchain technology evolves, we can expect to see more innovations in the space, including the integration of smart contracts and non-fungible tokens. These advancements will further enhance the capabilities of cryptocurrencies like Shiba Inu Coin, offering new opportunities for entrepreneurs and businesses alike.
Fundamentals of Ethereum Classic

– Ethereum Classic is a public, *decentralized* blockchain platform that runs smart contracts and allows for peer-to-peer transactions.
– It is a fork of the original Ethereum blockchain, created in response to the DAO hack in 2016.
– Ethereum Classic uses the same technology as Ethereum, including the Ethereum Virtual Machine (EVM) and a similar consensus algorithm.
– One of the key differences between Ethereum and Ethereum Classic is the philosophy regarding immutability.
– Ethereum Classic believes in the principle of “code is law,” meaning that transactions on the blockchain are irreversible.
– This makes Ethereum Classic appealing for applications where tamperproofing is crucial, such as contracts, data storage, and financial transactions.
– Understanding the fundamentals of Ethereum Classic is essential for anyone looking to work with blockchain technology, whether it’s for building applications, creating smart contracts, or participating in the cryptocurrency market.
Merkle Trees in Blockchain
Merkle Trees are an essential part of Blockchain technology, providing a way to efficiently verify the integrity of data within a block.
When transactions are added to a block, a Merkle tree is created by hashing pairs of transactions until a single root hash is obtained.
This root hash is then included in the block header, allowing for easy verification of the transactions within the block.
By using Merkle Trees, Blockchain can ensure the security and immutability of the data stored within each block.
Introduction to Cardano
Cardano is a **blockchain platform** that aims to provide a more secure and scalable infrastructure for **smart contracts** and **peer-to-peer transactions**. It was created to address some of the limitations of earlier blockchain technologies, such as Bitcoin.
One of the key features of Cardano is its focus on **decentralization** and **security**. This means that transactions on the Cardano network are verified by a network of nodes rather than a central authority, making it more resistant to **theft** and **fraud**.
Cardano also supports the creation of **non-fungible tokens** (NFTs), which are unique digital assets that can represent ownership of **goods and services**, artwork, or other items. This opens up new possibilities for **entrepreneurs** and **artists** to tokenize their creations.
Overview of Matic Network
The Matic Network is a layer 2 scaling solution that aims to improve the scalability and usability of the Ethereum blockchain. It achieves this by using sidechains to offload transactions from the main Ethereum chain, reducing congestion and lowering fees.
One of the key features of Matic Network is its Plasma framework, which enables faster and more efficient **peer-to-peer transactions**. This allows users to transfer assets quickly and securely without relying on intermediaries.
Matic Network also supports the development of decentralized applications (dApps) and smart contracts, making it a versatile platform for **application software**. By leveraging Matic’s technology, developers can create scalable and user-friendly blockchain solutions.
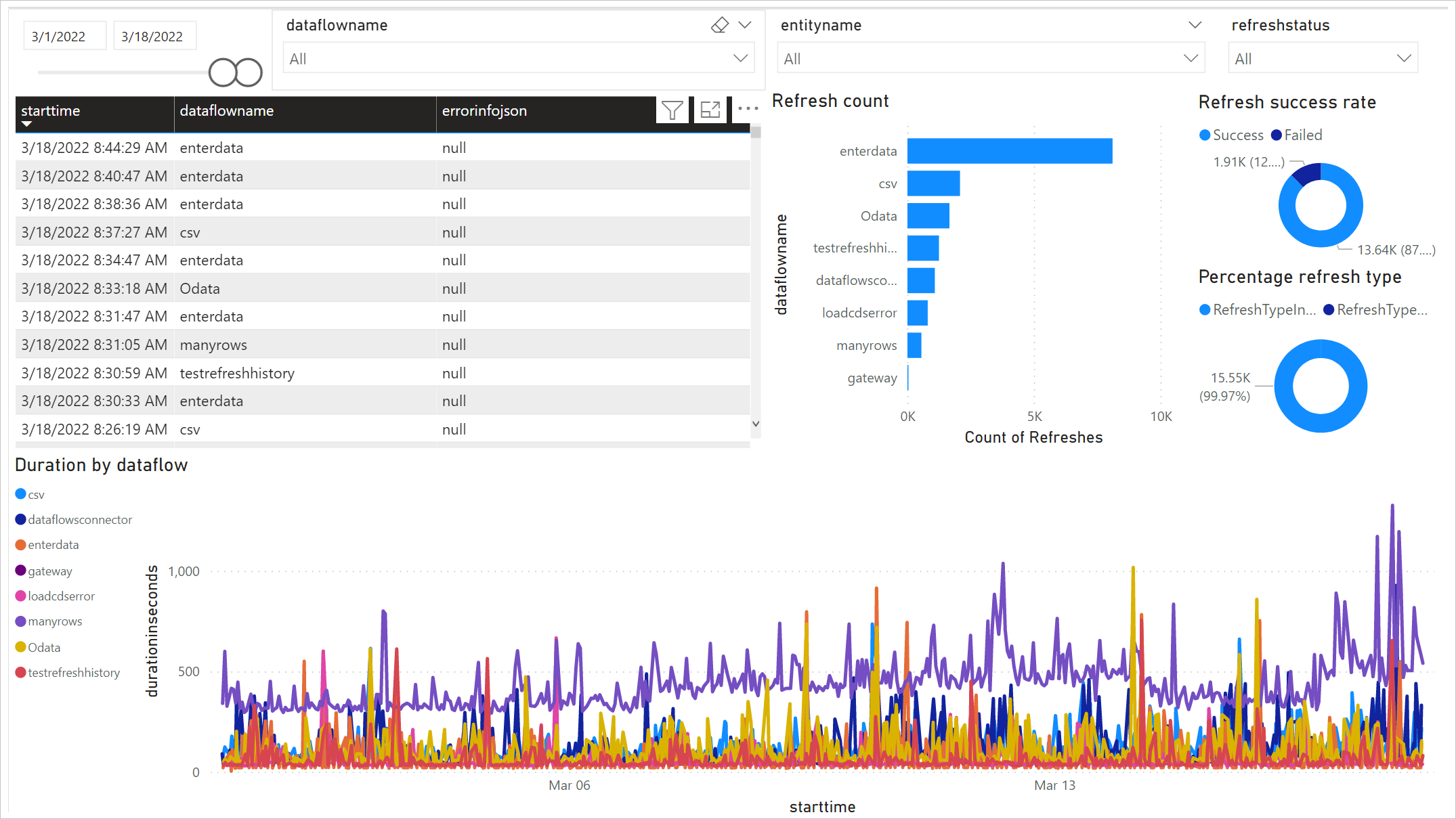
Top Blockchain Interview Questions
| Question |
Answer |
| 1. What is blockchain? |
Blockchain is a decentralized, distributed ledger technology that securely records transactions across a network of computers. |
| 2. How does blockchain work? |
Blockchain works by creating a chain of blocks that contain transaction data. Each block is linked to the previous block using cryptographic hashes. |
| 3. What are the key features of blockchain? |
The key features of blockchain include decentralization, transparency, immutability, and security. |
| 4. What is a smart contract? |
A smart contract is a self-executing contract with the terms of the agreement between buyer and seller directly written into lines of code. |
| 5. What is a cryptocurrency? |
A cryptocurrency is a digital or virtual currency that uses cryptography for security and operates independently of a central authority. |
Understanding Tether
Tether is a **cryptocurrency** that was created to provide stability in the volatile world of digital assets. It is known as a **stablecoin** because its value is pegged to a traditional currency, such as the US dollar. This means that 1 Tether will always be equal to 1 dollar.
Tether is often used by traders and investors as a way to quickly move funds between exchanges without having to go through the traditional banking system. It allows for **peer-to-peer transactions** that are fast and secure, making it an attractive option for many in the crypto community.
While Tether has faced some controversy and scrutiny in the past, it remains one of the most widely used stablecoins in the market today. Understanding how Tether works and its role in the cryptocurrency ecosystem is essential for anyone looking to navigate the world of digital assets.
NFT vs Crypto Comparison
NFTs and cryptocurrencies are both based on blockchain technology, but they serve different purposes. NFTs are unique digital assets that represent ownership of a specific item, while cryptocurrencies are digital currencies used for peer-to-peer transactions.
NFTs have gained popularity in the art and collectibles market, while cryptocurrencies like Bitcoin are used as a form of digital money. Cardano is a blockchain platform that supports both NFTs and cryptocurrencies.
When using cryptocurrencies, transactions are verified through a cryptographic hash function and stored in a Merkle tree. This allows for secure and transparent transactions without the need for a bank or intermediary.
On the other hand, NFT transactions may involve the transfer of ownership of digital assets like art, music, or even virtual real estate. Both NFTs and cryptocurrencies have opened up new opportunities for entrepreneurship and decentralized finance.
Exploring Web 3.0
Blockchain technology is the foundation of Web 3.0, revolutionizing the way data is stored and transactions are conducted. Understanding the basics of blockchain is essential for beginners looking to dive into this innovative field.
One of the key components of blockchain is its decentralized nature, which eliminates the need for a central authority like a bank to facilitate transactions. Instead, transactions are verified and recorded by a network of nodes, ensuring security and transparency.
Blockchain technology relies on cryptographic hash functions to secure data and prevent tampering, making it a highly secure way to store information. Learning about blockchain can open up opportunities in various industries, from finance to healthcare.
Taking a blockchain technology tutorial for beginners is a great way to start your journey into this exciting field and gain valuable skills that are in high demand. So, don’t hesitate to explore the world of blockchain and unlock its potential for your future success.
Different Types of Blockchains
– Public Blockchains: These blockchains are open to anyone, allowing for transparent and decentralized transactions. *Bitcoin* and *Ethereum* are examples of public blockchains that use a proof-of-work consensus mechanism.
– Private Blockchains: In contrast, private blockchains are restricted to a specific group of users, providing more control over who can participate in the network. These are commonly used by businesses for internal processes and data management.
– Consortium Blockchains: Consortium blockchains are a hybrid between public and private blockchains, where a group of organizations work together to maintain the network. This type is often utilized in industries where multiple parties need to share data and collaborate securely.
– Permissioned Blockchains: Permissioned blockchains require users to have explicit permission to participate in the network, ensuring that only authorized individuals can access and modify data. This provides a higher level of security compared to public blockchains.
Decentralized Finance (DeFi) Explained
Decentralized Finance (DeFi) is a concept within the blockchain industry that aims to recreate traditional financial systems using blockchain technology. In DeFi, financial services like lending, borrowing, and trading can be accessed without the need for intermediaries such as banks or brokers.
One of the key aspects of DeFi is the use of smart contracts, which are self-executing contracts with the terms of the agreement between buyer and seller directly written into code. This allows for automated transactions without the need for a third party.
DeFi platforms are built on blockchain networks like Ethereum, which provide a secure and transparent environment for financial activities. By leveraging decentralized technology, DeFi offers users greater control over their assets and the ability to participate in a global financial system without traditional barriers.
Introduction to Ripple
Ripple is a digital payment protocol that enables **real-time** cross-border transactions. It aims to make international money transfers more efficient and cost-effective by eliminating intermediaries. Ripple uses a decentralized network of **validators** to confirm transactions, rather than relying on a central authority.
One of the key features of Ripple is its native digital asset, XRP, which can be used as a bridge currency for converting one form of value to another. This helps facilitate seamless transactions between different fiat currencies. Ripple’s technology has gained popularity among banks and financial institutions for its speed and low fees.
Overview of Binance
Binance is one of the largest cryptocurrency exchanges in the world, offering a wide range of digital assets for trading. It was founded in 2017 by Changpeng Zhao and has quickly become a popular choice for both beginners and experienced traders alike.
One of the key features of Binance is its high liquidity, allowing users to easily buy and sell cryptocurrencies at competitive prices. The platform also offers a secure trading environment, with advanced security measures in place to protect users’ funds.
In addition to trading, Binance also offers a range of other services, such as staking, lending, and futures trading.