Unlocking the potential of AWS CDK, Secrets Manager offers a game-changing solution for managing sensitive information securely in the cloud.
Initializing AWS CDK Secrets Manager
Once the initialization is complete, you can define and manage your secrets within your CDK stack using AWS CDK constructs and resources. Remember to adhere to best practices for secure password management, such as enforcing strong passwords and rotating them regularly.
By leveraging AWS CDK Secrets Manager, you can securely store and retrieve sensitive information, such as database credentials or API keys, within your applications. This ensures that your secrets are encrypted and accessible only to authorized users or services.
With the initial setup complete, you can now proceed to define the necessary resources and permissions for your secrets within your CDK stack. Be sure to properly manage access keys and permissions to minimize security risks.
Configuring AWS CDK Secrets Manager
To get started, you’ll need to have the AWS Cloud Development Kit (CDK) installed on your system. The CDK provides a convenient way to define your infrastructure as code and automate the deployment process.
Once you have the CDK set up, you can use the command-line interface to configure the Secrets Manager. This powerful tool allows you to create and manage passwords, keys, and other sensitive data in a secure manner.
To configure the Secrets Manager, you’ll need to define a secret in your CDK template. This can be done using the JSON or C++ syntax, depending on your preference. You can specify the secret’s name, description, and other attributes to suit your needs.
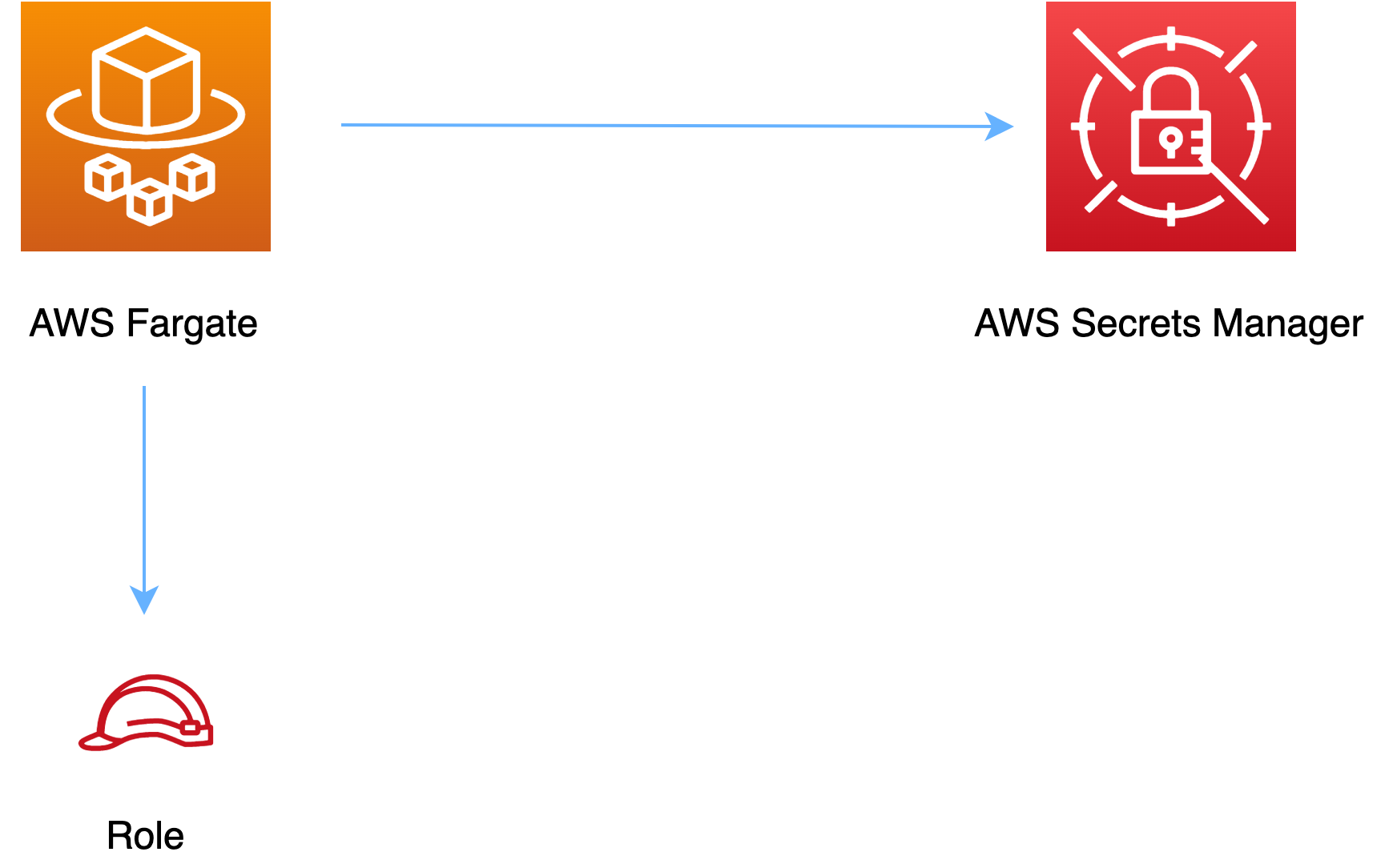
When configuring the secret, it’s important to consider access control and encryption. You can define an Identity and Access Management (IAM) policy to control who can access the secret and what actions they can perform. Additionally, you can encrypt the secret using AWS Key Management Service (KMS) for an extra layer of protection.
Once the secret is configured, you can use it in your applications or databases by retrieving its value from the Secrets Manager. This allows you to keep sensitive information separate from your code and easily manage it across different environments.
Managing Secrets in AWS CDK
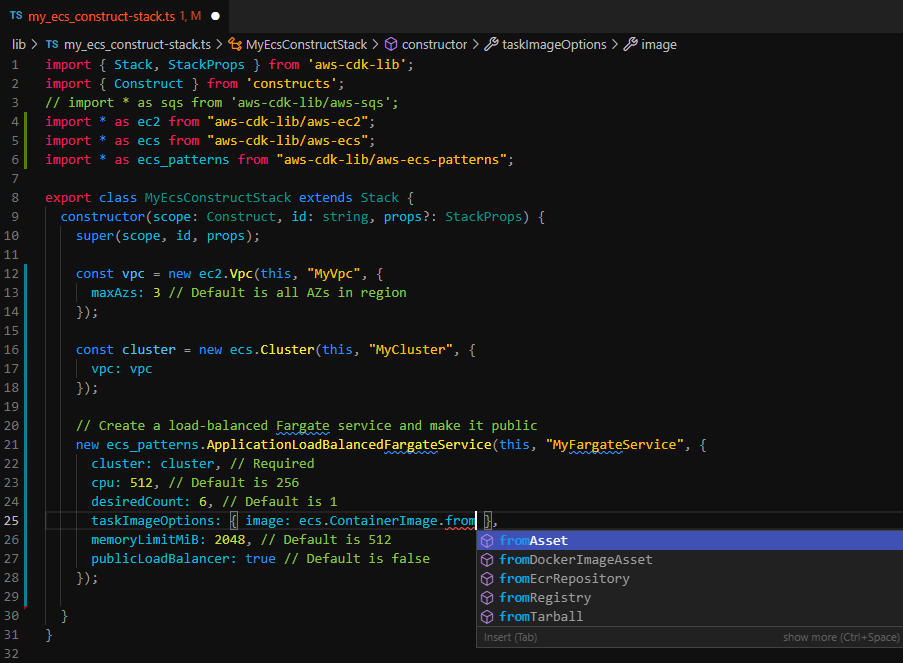
To work with Secrets Manager in AWS CDK, you can utilize the AWS SDKs or the command-line interface (CLI). You can create a secret using the Secrets Manager API and specify the secret’s name, description, and the secret value.
Once you have created a secret, you can retrieve its value using the AWS SDKs or CLI. The secret value is encrypted and stored securely by Secrets Manager. You can also rotate the secret value periodically to enhance security.
In your AWS CDK application, you can reference the secret by its ARN (Amazon Resource Name) and use it in your code or templates. This allows you to securely access sensitive information without exposing it directly in your code.
By leveraging Secrets Manager in AWS CDK, you can ensure the secure management of secrets in your cloud infrastructure, enhancing the overall security and integrity of your applications.
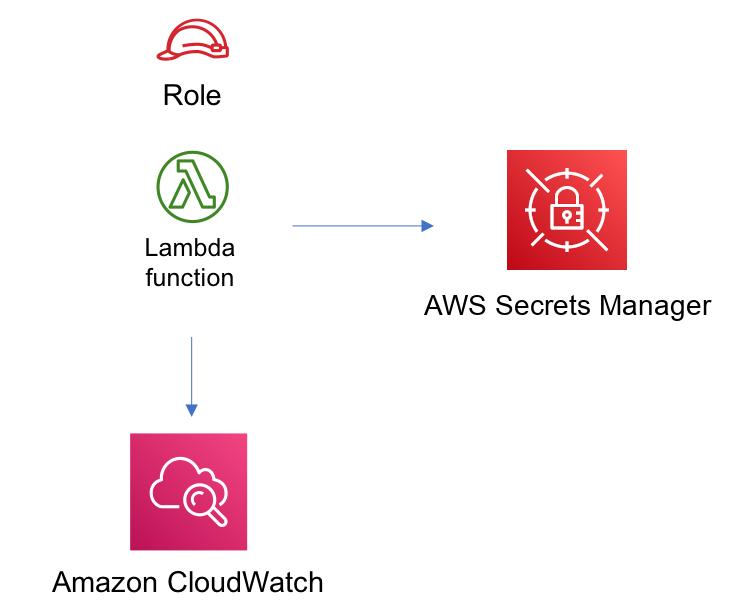
Customizing Secrets with Lambda Functions
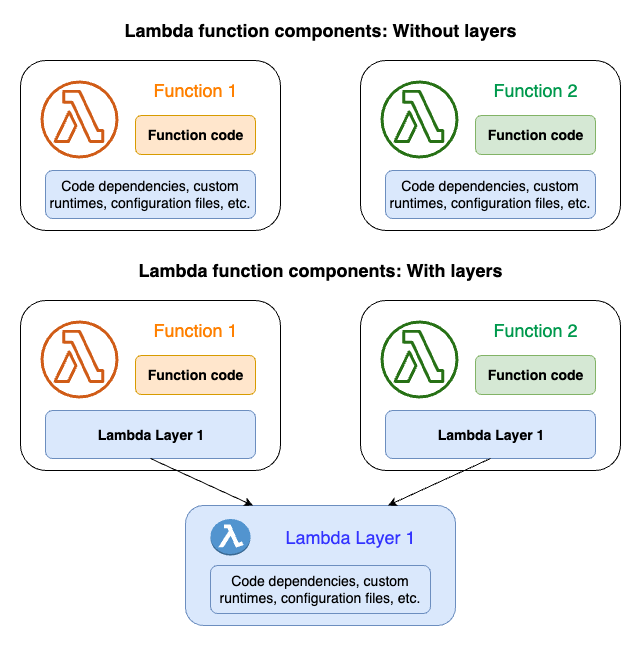
Lambda functions in AWS CDK Secrets Manager provide a powerful way to customize and enhance the management of secrets in your applications. With Lambda functions, you can automate the process of generating and rotating passwords, encrypting sensitive information, and managing access to secrets.
By leveraging the AWS CDK, you can easily create and deploy Lambda functions that interact with Secrets Manager. This allows you to define custom logic and workflows for your secrets, ensuring they meet your unique requirements.
For example, you can use Lambda functions to automatically generate strong passwords for your applications and rotate them periodically. You can also encrypt sensitive information before storing it in Secrets Manager, adding an extra layer of security to your data.
Furthermore, Lambda functions enable you to manage access to secrets by implementing custom identity management and user authentication mechanisms. This ensures that only authorized users or applications can access the secrets stored in Secrets Manager.
In addition, Lambda functions can be used to integrate with other AWS services, such as databases, to securely retrieve and store secret information. This allows you to seamlessly incorporate secrets into your application workflows without compromising security.
With AWS CDK Secrets Manager, you can easily customize your secrets management using Lambda functions, providing a flexible and secure solution for your applications.
(Note: CDK stands for Cloud Development Kit. It is a software development framework that allows you to define cloud infrastructure in code using familiar programming languages like C++ and JSON.)
Rotating Database Credentials with AWS CDK
Rotating database credentials is an essential security practice for any organization. With AWS CDK and Secrets Manager, managing and updating credentials becomes a breeze.
By leveraging the AWS Cloud Development Kit (CDK), developers can automate the rotation of database credentials and eliminate the need for manual intervention. This not only ensures better security but also saves time and effort.
Using Secrets Manager, credentials can be stored securely and accessed programmatically. The CDK allows you to define and deploy the necessary resources, such as secrets, users, and permissions.
With a simple C++ template, you can define the rotation schedule, password complexity requirements, and encryption settings. Secrets Manager takes care of generating and storing the passwords securely.
By rotating credentials regularly, you reduce the risk of unauthorized access and potential data breaches. With AWS CDK and Secrets Manager, you can easily implement a robust and automated credential rotation process.
Don’t compromise on security; leverage the power of AWS CDK and Secrets Manager to protect your database credentials effectively.
Importing and Replicating Secrets

Replicating secrets is also simple with AWS CDK Secrets Manager. You can create a new secret using the `Secret.fromSecretAttributes` method and provide the secret attributes such as name, description, and encryption key. This allows you to replicate secrets across different AWS accounts or regions.
By utilizing these methods, you can easily import and replicate secrets in AWS CDK Secrets Manager, enhancing the security and management of your applications. Take advantage of the powerful features provided by AWS CDK Secrets Manager and simplify your secret management process.
Creating JSON Secrets with AWS CDK
To create JSON secrets, you’ll need to define a Secret in your AWS CDK code. This Secret object will contain the secret value, which can be a plaintext string or a JSON object. You can also specify the secret name, description, and other optional parameters.
Once you’ve defined the Secret, you can deploy it using the AWS CDK. The secret value will be encrypted and securely stored in the AWS Secrets Manager service.
When your application needs to access the secret, you can retrieve it using the AWS SDK or AWS CLI. This allows you to securely access and use the secret within your application without exposing the sensitive information.
By utilizing the AWS CDK Secrets Manager, you can easily manage and securely store JSON secrets, ensuring the confidentiality of your application’s sensitive data.
Updating Lambda Function Code in AWS CDK
To update the code of a Lambda function in AWS CDK, follow these steps:
1. Open the AWS CDK project that contains the Lambda function.
2. Locate the specific Lambda function you want to update in the code.
3. Make the necessary changes to the code using the programming language of your choice (e.g., C++).
4. Save the updated code file.
5. Run the CDK deploy command to deploy the changes to AWS.
6. AWS CDK will automatically detect the changes in the code and update the Lambda function.
7. Verify the changes by testing the Lambda function with sample inputs.
8. If any errors occur during the update, review the error message and make the necessary corrections.
Best Practices and Limitations for AWS CDK Secrets Manager
| Best Practices | Limitations |
|---|---|
| 1. Use separate secrets for different environments (dev, prod, etc.) | 1. Secrets can only be created in the same AWS region where CDK is running |
| 2. Store sensitive data in Secrets Manager instead of hardcoding in the code | 2. Secrets Manager has a maximum limit of 64 KB per secret value |
| 3. Implement fine-grained access control for secrets using IAM policies | 3. Secrets Manager has a limit of 300 concurrent requests per account |
| 4. Rotate secrets regularly to enhance security | 4. Secrets Manager is not available in all AWS regions |
| 5. Use encryption at rest and in transit for secrets | 5. Secrets Manager cannot be used with all AWS services |