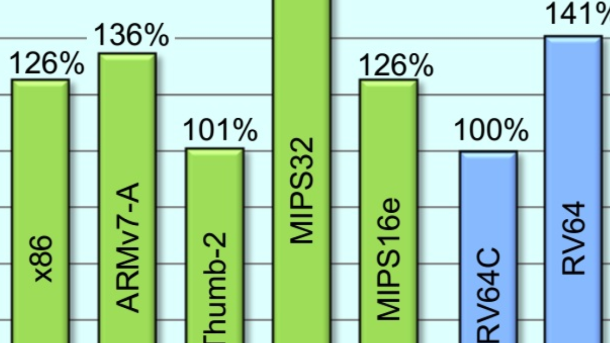
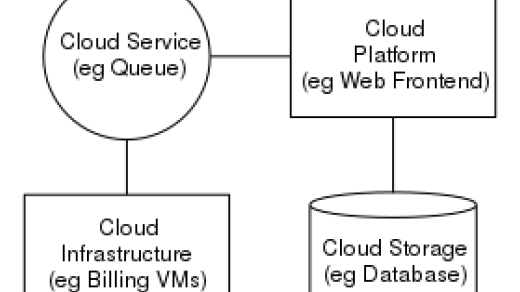
Welcome to the ultimate guide to understanding the revolutionary RISC-V architecture. In this tutorial, we will explore the basics of RISC-V design, its benefits, and how it is shaping the future of computing. Let’s dive in!
Design Principles and Instruction Set of RISC-V
RISC-V, a popular open-source instruction set architecture, follows the Reduced Instruction Set Computing (RISC) design principles.
This architecture is known for its simplicity, modularity, and flexibility, making it ideal for a wide range of applications from embedded systems to supercomputers.
RISC-V features a small set of instructions, which allows for efficient energy use and easier program optimization.
By focusing on simplicity and standardization, RISC-V enables innovation and encourages the development of new applications and technologies in the computing industry.
Register File and Memory Model in RISC-V
The **Register File** and **Memory Model** in **RISC-V** play crucial roles in the overall architecture of the system. The **Register File** stores temporary data that the central processing unit (CPU) needs to access quickly during execution.
On the other hand, the **Memory Model** is responsible for managing the data stored in the system’s memory and ensuring efficient access to it. Understanding how these components work together is essential for optimizing the performance of a **RISC-V** system.
By familiarizing yourself with the **Register File** and **Memory Model**, you can gain a deeper understanding of how instructions are processed and data is stored within the **RISC-V** architecture. This knowledge is invaluable for anyone looking to work with **RISC-V** based systems or develop software for them.
Mastering the intricacies of the **Register File** and **Memory Model** will enable you to write more efficient code and make better use of the system’s resources. Whether you are a seasoned developer or just getting started with **RISC-V**, a solid grasp of these concepts is essential for success in the field.
Privilege Levels and Implementations in RISC-V
Privilege levels in RISC-V refer to the different modes of access and control that the processor provides to different parts of the system. These levels include *machine mode* for system maintenance and bootstrap, *supervisor mode* for operating system control, and *user mode* for application execution.
Implementations in RISC-V allow for flexibility in how these privilege levels are utilized and managed within the system. This can vary depending on the specific design choices made by the processor manufacturer and the intended use case of the system.
Understanding privilege levels and their implementations in RISC-V is crucial for developers working on low-level system software, such as operating systems or embedded systems. By mastering these concepts, developers can optimize performance, security, and resource management in their applications.
Ecosystem, Community, and Applications of RISC-V
The RISC-V architecture has a thriving ecosystem, with a strong community of developers and users driving its growth. Open-source software plays a key role in the RISC-V community, fostering collaboration and innovation.
Applications of RISC-V span a wide range of fields, from embedded systems to supercomputers. This versatility makes RISC-V a popular choice for various projects, including artificial intelligence and Internet of Things (IoT) applications.
Advantages and Disadvantages of RISC-V
| Advantages | Disadvantages |
|---|---|
| Open-source architecture, allowing for customization and innovation | Lack of market penetration compared to established architectures like ARM |
| Scalability, with different instruction set options for different applications | Potential compatibility issues with existing software and tools |
| Energy-efficient design, leading to lower power consumption | Less mature ecosystem compared to other architectures |
| Reduced complexity and streamlined instruction set, leading to faster execution | Limited availability of RISC-V hardware and development tools |
RISC-V Cores: Building Open Source Derivatives

RISC-V cores are the foundation of open-source derivatives, allowing for customizable and efficient processor design. By leveraging the RISC-V architecture, developers have the flexibility to create CPUs tailored to specific needs.
With RISC-V, users can access a wide range of **open-source** resources to build their derivatives, ensuring transparency and modularity in the design process. This approach promotes collaboration and standardization within the industry, fostering innovation and advancement in computer architecture.
Whether you are working on embedded systems, artificial intelligence, or supercomputing projects, RISC-V cores offer a scalable and adaptable solution. By understanding the intricacies of RISC-V architecture, developers can optimize performance, energy efficiency, and security in their designs.
Explore the possibilities of RISC-V cores and unleash the potential of open-source processor development. Embrace the future of computing with RISC-V and take your projects to the next level of efficiency and intelligence.