In an increasingly connected and digital world, the importance of cybersecurity cannot be overstated. As organizations strive to protect their valuable data and systems from sophisticated cyber threats, hiring professionals well-versed in this field becomes crucial. This article explores some of the top cybersecurity interview questions that can help employers assess the knowledge, skills, and experience of potential candidates.
Understanding Cryptography and Encryption

Cryptography and encryption are essential components of information security and computer network protection. They play a crucial role in safeguarding sensitive data and preventing unauthorized access. In a cybersecurity interview, you may be asked about your understanding of these concepts and their practical applications.
Cryptography is the science of secure communication, while encryption is the process of converting plain text into unreadable ciphertext using an encryption algorithm and a secret key. It ensures that data remains confidential and protected from cyberattacks, such as brute-force attacks or man-in-the-middle attacks.
There are two main types of cryptography: symmetric-key and public-key cryptography. Symmetric-key algorithms use the same key for both encryption and decryption, while public-key cryptography involves a pair of keys, one for encryption and the other for decryption.
In the context of cybersecurity, it is important to have a good understanding of encryption algorithms, such as Advanced Encryption Standard (AES), Triple DES, and cryptographic hash functions like SHA-256. These algorithms are used to secure data transmission and storage, ensuring data integrity and preventing unauthorized modifications.
In addition to encryption, other cybersecurity measures like firewalls, intrusion detection systems, and virtual private networks (VPNs) are used to protect computer networks and secure sensitive information. Familiarity with these tools and concepts is essential for a successful career in cybersecurity.
When discussing cryptography and encryption in a cybersecurity interview, it is important to showcase your knowledge of best practices and industry standards. This may include topics like password strength, multi-factor authentication, and the proper management of cryptographic keys.
Exploring Firewalls and Network Security
![]()
When it comes to cybersecurity interview questions, one important area to focus on is firewalls and network security. Employers want to ensure that candidates understand the key concepts and best practices related to protecting computer networks from unauthorized access and potential cyberattacks. Some potential questions in this area may include:
– Can you explain how a firewall works and its role in network security?
– What are some common types of firewalls and their differences?
– How can firewalls be used to prevent unauthorized access to a computer network?
– What is the purpose of an intrusion detection system and how does it work alongside a firewall?
– Can you discuss the importance of strong passwords and password management in network security?
– What are some potential vulnerabilities that firewalls can help protect against?
– Have you ever conducted or been involved in a penetration test? If so, can you share your experience and the results?
These questions help gauge a candidate’s knowledge and experience in the field of network security. It is important for candidates to be able to articulate their understanding of firewalls and how they contribute to overall information security.
Differentiating Between IDS and IPS
An Intrusion Detection System (IDS) and an Intrusion Prevention System (IPS) are both crucial components of computer security. While they serve similar purposes, there are key differences between the two.
An IDS is designed to monitor network traffic and identify potential security breaches. It analyzes data packets, looking for patterns or signatures of known threats. When an IDS detects suspicious activity, it generates an alert for further investigation. IDSs operate at the network level of the OSI model, making them effective at detecting attacks across multiple systems.
On the other hand, an IPS goes a step further by actively blocking and preventing suspicious activity. It can automatically respond to detected threats, blocking malicious traffic or reconfiguring network settings to protect against attacks. IPSs operate at the superuser level, which allows them to take immediate action to protect the system.
Unraveling the Difference Between VA and PT
When it comes to cybersecurity, understanding the difference between a Virtual Assistant (VA) and a Penetration Tester (PT) is crucial.
A VA is responsible for managing administrative tasks and providing support remotely. They may help with tasks like scheduling, email management, and data entry. On the other hand, a PT is a cybersecurity professional who tests the security of a system by attempting to exploit vulnerabilities.
While a VA focuses on day-to-day operations, a PT focuses on identifying weaknesses in a system’s defenses. They perform tasks such as vulnerability scanning, penetration testing, and ethical hacking to ensure the security of a network or system.
In terms of training, Linux knowledge is essential for both roles. Linux is widely used in the cybersecurity field due to its security features and flexibility. Taking Linux training courses can provide individuals with the necessary skills to excel in either role.
Whether you’re interested in becoming a VA or a PT, Linux training can help you gain a solid foundation in computer security and the OSI model. It can also familiarize you with concepts such as malware, cross-site scripting, computer viruses, and encryption algorithms.
The Importance of SSL and TLS Encryption
![]()
SSL and TLS encryption are essential components of cybersecurity. They provide a secure and encrypted connection between a client and a server, ensuring the confidentiality and integrity of data transmitted over the internet. Without SSL and TLS, sensitive information such as passwords, credit card details, and personal data can be intercepted and compromised by malicious actors.
By implementing SSL and TLS, organizations can protect themselves from various cyber threats such as man-in-the-middle attacks, data interception, and unauthorized access. These encryption protocols establish a secure “handshake” between the client and server, verifying the authenticity of the server and encrypting the data exchanged between them.
In the context of Linux training, understanding how SSL and TLS work is crucial for individuals pursuing a career in cybersecurity. Linux is widely used in server environments, and knowledge of SSL and TLS encryption is necessary to configure secure connections and protect sensitive data.
Employers often ask interview questions related to SSL and TLS encryption to assess a candidate’s understanding of cybersecurity principles and their ability to implement secure solutions. Some common interview questions may include:
1. How does SSL/TLS encryption work?
2. What are the differences between SSL and TLS?
3. What is the role of SSL certificates in securing web communications?
4. How can you configure SSL/TLS on a Linux server?
5. What are some common vulnerabilities associated with SSL/TLS encryption?
6. How can you protect against man-in-the-middle attacks when using SSL/TLS?
Having a solid understanding of SSL and TLS encryption, along with other cybersecurity concepts, will make an individual a valuable asset in the field. It is important to stay updated with the latest best practices and technologies to effectively protect against cyber threats and secure sensitive information.
Preventing Brute Force and SQL Injection Attacks
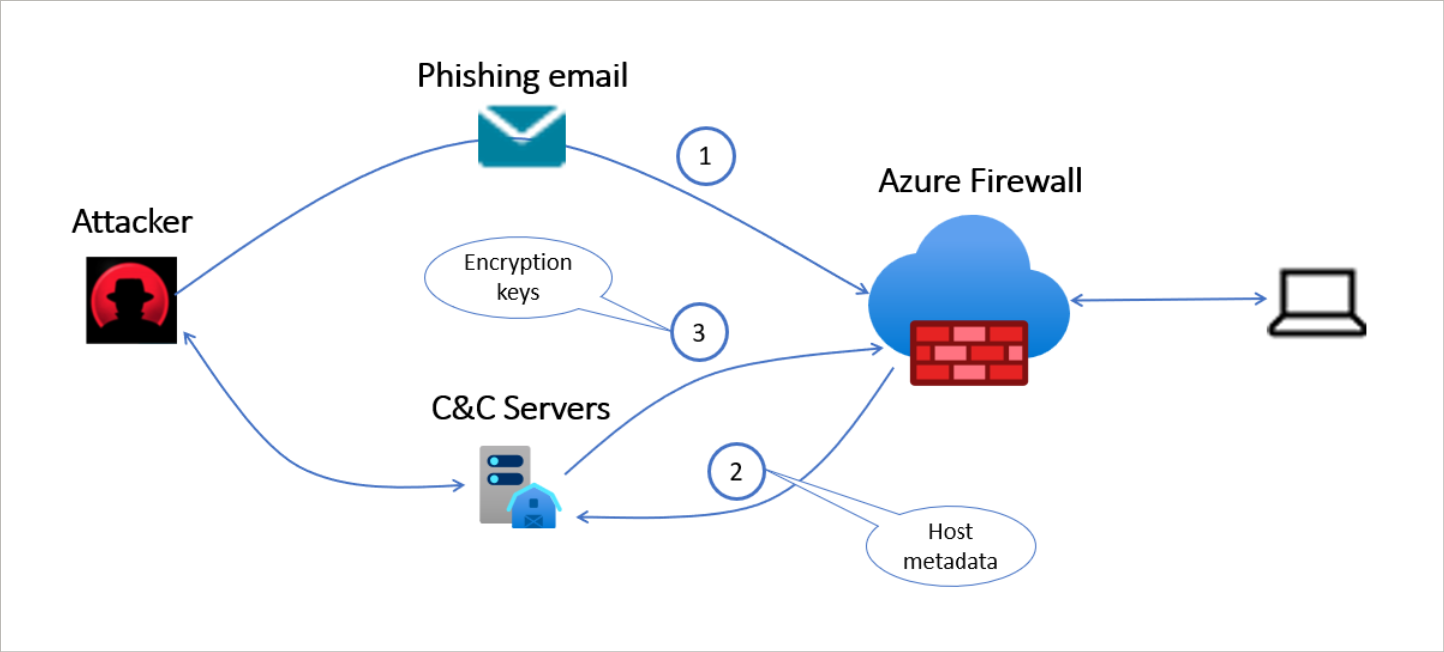
To protect your system from Brute Force and SQL Injection Attacks, there are a few important measures you can take. Firstly, ensure that you have strong password policies in place, enforcing the use of complex passwords with a combination of uppercase and lowercase letters, numbers, and special characters. Implementing multi-factor authentication adds an extra layer of security, requiring users to provide additional verification beyond just a password.
Regularly updating and patching your software is crucial to prevent vulnerabilities that attackers may exploit. Utilize a firewall to monitor and control incoming and outgoing network traffic, preventing unauthorized access to your system. Employing an Intrusion Detection System (IDS) can also help detect and alert you to any suspicious activity or attacks.
It is essential to regularly back up your data to a secure location to ensure data integrity and availability. This will allow you to restore your system in case of a successful attack.
Additionally, consider implementing a Web Application Firewall (WAF) to protect against common web-based attacks such as Cross-site scripting and SQL Injection.
Understanding Port Scanning and ARP
Port scanning and ARP (Address Resolution Protocol) are important concepts in cybersecurity.
Port scanning involves scanning a computer or network to identify open ports and services. It is often used by hackers to identify potential vulnerabilities and gain unauthorized access. By understanding port scanning techniques, you can better protect your system and network from malicious attacks.
ARP is a protocol used to map an IP address to a physical MAC address on a local network. It is essential for communication between devices within the same network. Understanding how ARP works can help you identify and prevent ARP spoofing attacks, where an attacker impersonates another device on the network.
By familiarizing yourself with port scanning and ARP, you can enhance your cybersecurity knowledge and be better prepared to defend against potential threats. Linux training can provide you with the necessary skills to effectively secure your systems and networks.
The Role of Two-Factor Authentication and VPNs

Two-factor authentication and VPNs play a crucial role in enhancing cybersecurity. Two-factor authentication adds an extra layer of security by requiring users to provide two forms of identification, such as a password and a unique code sent to their mobile device. This helps protect against unauthorized access and reduces the risk of credential theft. VPNs, or virtual private networks, create a secure and encrypted connection between a user’s device and the internet. This safeguards sensitive data and prevents eavesdropping or interception from malicious actors.
By implementing these measures, individuals and organizations can significantly strengthen their defenses against cyber threats.
Identifying Different Types of Hackers
There are several types of hackers, including black hat hackers who engage in illegal activities for personal gain or malicious purposes. On the other hand, white hat hackers, also known as ethical hackers, use their skills to identify vulnerabilities and help improve security measures.
Other types include gray hat hackers, who fall somewhere in between black and white hat hackers, and script kiddies, who lack advanced skills but use pre-written scripts to carry out attacks.
Understanding these distinctions can help organizations assess potential threats and develop appropriate defense strategies. It is also important to note that hackers can target various areas, such as networks, websites, or individuals, making it crucial to have a comprehensive cybersecurity approach.
Patch Management and its Importance
Patch management is a crucial aspect of cybersecurity. It involves regularly updating software and systems to address any vulnerabilities or weaknesses that may be exploited by hackers or malware. By keeping software up to date with the latest patches, organizations can significantly reduce the risk of cyberattacks and unauthorized access.
Superuser privileges are often required to install patches, so it’s important to ensure that only authorized individuals have access to these privileges. Additionally, organizations should have a clear process in place for testing and deploying patches to minimize disruptions to operations.
Regular patch management is especially important for Linux systems, as they are often targeted by hackers due to their widespread use and open-source nature. Linux training can help individuals gain the knowledge and skills needed to effectively manage patches and maintain the security of Linux-based systems.
In an interview, candidates may be asked about their experience with patch management and their understanding of its importance. Employers will want to know if candidates are familiar with best practices for patch management, such as prioritizing critical patches and scheduling regular updates. They may also ask about candidates’ knowledge of common vulnerabilities and how they would address them through patch management.
Preventing Phishing and XSS Attacks
Phishing and XSS attacks are common cybersecurity threats that can compromise sensitive information and cause significant damage. To prevent these attacks, it is crucial to follow best practices and implement robust security measures.
1. Educate users: Train employees and users to recognize phishing emails and suspicious websites. Teach them how to identify common phishing techniques, such as spoofed URLs and requests for personal information.
2. Implement strong authentication: Require strong passwords and consider implementing multi-factor authentication. This adds an extra layer of security and makes it harder for attackers to gain unauthorized access.
3. Keep software updated: Regularly update operating systems, web browsers, and software to patch vulnerabilities that attackers could exploit. Enable automatic updates whenever possible to ensure the latest security features are in place.
4. Use web filters and firewalls: Implement web filters to block access to known malicious websites and use firewalls to monitor and control network traffic. This helps prevent users from inadvertently visiting phishing sites or downloading malicious content.
5. Regularly backup data: Create and maintain regular backups of important data. This helps mitigate the impact of potential attacks and allows for quick recovery in case of data loss.
Exploring DDoS Attacks and Botnets
DDoS attacks and botnets are major threats in the cybersecurity landscape. Understanding how these attacks work is crucial for anyone interested in Linux training and a career in cybersecurity.
A DDoS (Distributed Denial of Service) attack floods a target server with a massive amount of internet traffic, making it unavailable to legitimate users. This can be done using a botnet, a network of compromised devices controlled by a hacker.
To protect against DDoS attacks and botnets, Linux professionals should be familiar with techniques like rate limiting, traffic filtering, and implementing firewalls. Additionally, knowledge of network security protocols like Transport Layer Security (TLS) and Virtual Private Networks (VPNs) is essential.
Linux professionals should also be well-versed in password strength and credential management. Weak passwords can be easily cracked using brute-force attacks, compromising an entire system. Implementing strong password policies and multi-factor authentication can mitigate this risk.
Moreover, understanding the fundamentals of cryptography, including symmetric-key algorithms and cryptographic hash functions, is crucial. These concepts are used to secure sensitive data and communications.
Data Protection in Transit vs Data Protection at Rest

| Data Protection in Transit | Data Protection at Rest | |
|---|---|---|
| Definition | Data protection measures applied when data is being transmitted over a network. | Data protection measures applied when data is stored or at rest in storage devices. |
| Focus | Ensuring data remains secure during transmission between systems or networks. | Protecting data while it is stored or at rest in databases, servers, or other storage devices. |
| Encryption | Data encryption is crucial to protect data while it travels over the network. | Data encryption may or may not be used, depending on the sensitivity and requirements of the stored data. |
| Transport Protocols | Secure protocols like HTTPS, SSL/TLS, SSH, VPN, etc. are commonly used. | Transport protocols like HTTP, FTP, etc. may be used, but encryption is not mandatory. |
| Security Measures | Firewalls, Intrusion Detection Systems (IDS), Intrusion Prevention Systems (IPS), etc. are employed. | Access controls, encryption, strong authentication, backup and recovery, etc. are implemented to secure the data at rest. |
Implementing 2FA for Public Websites
Implementing 2FA (two-factor authentication) for public websites is an essential step in enhancing their security. By requiring users to provide two forms of identification, such as a password and a unique code sent to their mobile device, 2FA significantly reduces the risk of unauthorized access. This extra layer of protection helps mitigate the threat of cyberattacks, including brute-force attacks and identity theft.
To implement 2FA, website owners can utilize various methods, such as SMS authentication, app-based authentication, or hardware tokens. Each method has its advantages and considerations, so it’s important to choose the one that best fits the website’s needs and user experience.
When implementing 2FA, it is crucial to educate users about its benefits and guide them through the setup process. Clear instructions and user-friendly interfaces can help users understand and adopt this additional security measure. Regularly updating the 2FA system and monitoring its effectiveness is also important to stay ahead of potential vulnerabilities.
Understanding Cognitive Cybersecurity
Cognitive cybersecurity is a critical aspect of protecting computer systems and networks from cyber threats. It involves understanding and analyzing the human element in cybersecurity, including how individuals think and make decisions that may impact security.
When it comes to cybersecurity interview questions, understanding cognitive cybersecurity can be highly relevant. Employers may ask questions to assess your knowledge and skills in this area, such as how you would address human vulnerabilities or how you would educate users on best security practices.
To prepare for these questions, it is important to familiarize yourself with concepts such as social engineering, phishing attacks, and the psychology of human behavior in relation to cybersecurity. Additionally, having a strong understanding of technical concepts like encryption, firewalls, and network security protocols can also be beneficial.
By demonstrating your knowledge of cognitive cybersecurity, you can showcase your ability to address both technical and human vulnerabilities in a comprehensive manner. This can make you a valuable asset to any organization looking to enhance their cybersecurity measures.
Exploring VPN vs VLAN
VPN and VLAN are both important tools in the field of cybersecurity. A VPN, or Virtual Private Network, is a secure connection that allows users to access a private network over a public network, such as the internet. It encrypts the data being transmitted, making it secure and protecting it from potential cyberattacks. On the other hand, a VLAN, or Virtual Local Area Network, is a logical grouping of devices on a network, creating separate segments that enhance security and performance.
When it comes to choosing between VPN and VLAN, it depends on the specific needs and goals of the organization. If the main concern is secure remote access to the network, a VPN is the best choice. It creates a secure tunnel for data transmission, protecting it from interception by unauthorized users. On the other hand, if the main concern is segregating and isolating network traffic, a VLAN is the way to go. It allows for better network management and control by dividing the network into smaller segments.
Social Engineering and Security Policies
Some common questions you may encounter include:
1. How would you define social engineering in the context of cybersecurity?
2. What are some common social engineering techniques and how can they be prevented?
3. How can security policies help mitigate the risks associated with social engineering attacks?
4. Can you provide examples of security policies that address social engineering vulnerabilities?
5. How would you educate employees about the dangers of social engineering and the importance of following security policies?
When answering these questions, it is important to demonstrate a clear understanding of social engineering tactics, such as phishing, pretexting, and tailgating. Discuss how security policies, such as strong password requirements, user awareness training, and access control measures, can help prevent and mitigate social engineering attacks. Additionally, highlight the importance of ongoing education and awareness programs to keep employees informed and vigilant against social engineering threats.
The Role of Artificial Intelligence in Cybersecurity
Artificial Intelligence (AI) plays a crucial role in cybersecurity, helping to protect systems from cyber threats. Cybersecurity professionals can leverage AI to detect and respond to attacks more effectively. AI-powered tools can analyze vast amounts of data and identify patterns that indicate potential threats, such as malware or unusual network activity. These tools can also automate processes like penetration testing and security monitoring, freeing up time for professionals to focus on more complex tasks. AI can assist in securing networks and systems by identifying vulnerabilities and implementing best practices to mitigate risks.
It also helps in quickly detecting and responding to cyberattacks, minimizing the potential damage.



